Intrusion Detection System and its Types in Machine learning
An Intrusion Detection System – or (IDS) we may say – can systematically be monitoring the network traffic – for identifying the suspicious activity[ies] and generating alerts – at times the issues are discovered.
Moreover, many of the QuickBooks Hosting Providers prefer to call it a software application that can unstopabbly scan the available network or the system – either for harmful activities [like the policy breaching].
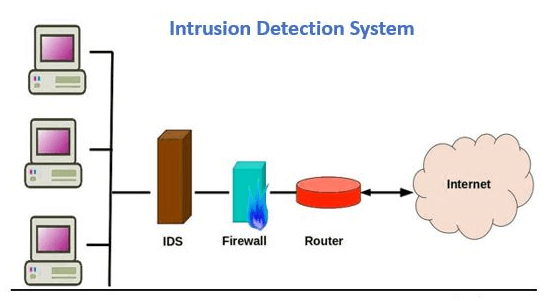
If there is any malicious venture or violation that can normally be reported – either to an administrator – or collected centrally – with the effective use of the available security information, this event-detection management system can undoubtedly integrate the outputs – from multiple sources.
Primarily, the experts must not hesitate in using its alarm-filtering techniques – for differentiating the malicious activities from false alarms.
Classification of Intrusion Detection System as per ML principles
Though the intrusion detection systems may monitor well the networks for identifying the potential malicious activities, yet they are primarily disposed to false alarms. Henceforth, the organizations must never delay the fine-tuning of their IDS products – whenever the workers had installed them first.
This signifies the fact that the proper setting-up of the intrusion detection systems will offer helping hands in recognizing what the normal traffic – on the available network(s) – will be looking like – as compared to the current or the futuristic malicious activities.
Indistinguishably, the Intrusion prevention systems will feasibly be monitoring the network packets inbound[ing] the system – thereby investigating the malicious activities involved in it. Later, the administrators may successfully be sending the warning notifications.
And, it is much needed – for drawing the sub-divisions of IDS: –
# Sub-Division Number One – Network Intrusion Detection System
Network intrusion detection systems – or(NIDS) – must be settled-up at the planned points – within the network – the sole purpose will be the examination of traffic from all devices relying upon the network. Later, it will be performing an observation of passing traffic on the entire subnet and then, validating the traffic that will pass on the subnets – for collecting the known-attacks.
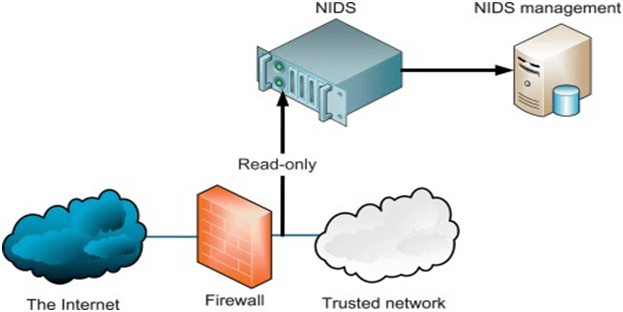
Once the attack will be identified or any sort of abnormalities is observed, the alert will assertively be sent to the administrator. If you are one of those knotted with Cloud QuickBooks hosting, you will be amazed to know about the example of NIDS – this will be – installing the system on the subnet where firewalls can be identified – for investigating if someone is trying to crack the installed firewall(s).
# Sub-Division Number Two – Host Intrusion Detection System
Host intrusion detection systems – or (HIDS) – will be unstoppably running on the independent hosts or devices accessing the network-resources.
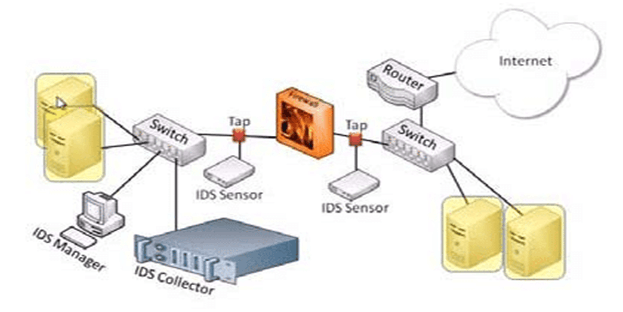
If we dive deeper, we may be concluding that a HIDS will be monitoring the outgoing and incoming packets – from the devices only; thereby alerting the administrators – if in case – the suspicious or malicious activity was detected. One must not ignore the fact that such administrators may be the one whole-heartedly inclined towards Qb Hosting.
Indistinguishably, the system won’t be taking longer in clicking the snapshots of the existing system-files and later, comparing them with the previous ones. If in case, the analytical system files were selected for editing or deleting purposes, an alert will be propagated to the administrator – for further investigations.
An example of HIDS usage will be seen on the mission-critical machines, which won’t be changing their layouts – as per the ML experts’ point-of-view.
# Sub-Division Number Three – Protocol-based Intrusion Detection System
A protocol-based intrusion detection system – or (PIDS) – will be comprised of a system or an agent that would consistently be residing at the server’s front end, to interpret and control the protocols between the server and a user/device – for the most obvious reasons.
From the ML perspective, the PIDS will be trying to secure the web-server – by regularly monitoring the HTTPS protocol streams and conclusively, accepting the related HTTP protocols.
With many assertions, the HTTPS may be identified un-encrypted and before this may instantly enter in the available web- presentation layer, then this system would be commanding itself – for residing in this interface.
Such interfaces may be spotted in between – so that PIDS will be using the award-winning benefits of HTTPS protocols.
# Sub-Division Number Four – Application Protocol-based Intrusion Detection System
Application Protocol-based Intrusion Detection System – or (APIDS) – is such a system or an agent – that will generally be residing – within a group of servers.
Even the ones boldly inclined towards QuickBooks Cloud and its relevant add-ons won’t be denying the fact that the system can identify the intrusions thereby, monitoring and interpreting, the communication on various application-specific protocols.
For instance, this would be monitoring the SQL protocols – explicitly – to the middleware – since the system will be transacting well – with the available databases -residing within the web-servers.
# Sub-Division Number Five – Hybrid Intrusion Detection System
The hybrid intrusion detection system – or(HIDS) – is made after combining two or more approaches of the outstanding intrusion detection systems.
If one can understand well, the hybrid intrusion detection system can synchronize well with the host agent or system data – and then, combining with network information – for developing a complete three-sixty-degree view of the network system.
For better clarity, we may say that a Hybrid intrusion detection system will be much more effective – if the same is compared to the other intrusion detection systems. Prelude may be exemplified as a Hybrid IDS.
Is there a need for a comparison of IDS with the connected firewalls?
An IDS or the connected firewall can be related to reliable network security. But, if one needs to draw lines of comparisons, an IDS will somewhere be differing from the connected firewalls – since a firewall will be looking outwardly – for unplanned intrusions – with the only purpose that the intrusions may be stopped somehow.
Moreover, you may be spotting the firewalls in the QuickBooks Remote Desktop services – this is because the Qb developers can anytime restrict the access between the available networks – for preventing intrusions.
And, if in case, an attack occurs from inside the network, the systems might fail to reciprocate the signals.
Therefore, an IDS can undoubtedly be describing a suspected intrusion – once the same has happened and then, signaling the alarm – for preventing further damages. So, one need not draw many comparisons between the IDS and the connected firewalls.

